Top 10 API Discovery Tools to Secure Your Applications in 2025


.svg)

APIs are at the center of modern software development, enabling systems to communicate and share data across applications and services. As organizations expand through microservices and AI-driven development, the number of APIs skyrockets, often without proper oversight. Many remain undocumented or forgotten, creating blind spots that attackers can exploit, and turning API awareness into a key element of application security.
API discovery tools address this challenge by automatically identifying and cataloging every API across an organization’s environment. They give security and development teams a clear understanding of what exists, how each API behaves, and what data it interacts with. In 2025, discovery has become an essential layer of defense, using automation and contextual analysis to keep pace with continuous code changes and the rapid expansion of enterprise APIs.
As API ecosystems expand across clouds, microservices, and development pipelines, discovery platforms have evolved to address visibility gaps in different ways. The tools below represent the leading approaches in 2025, covering code-based, traffic-based, and hybrid discovery methods designed for varied deployment needs and security goals.
Pynt is a leading API Discovery and Security Testing platform, helping organizations uncover and secure APIs directly within the development lifecycle. It maps APIs through source code inspection and live traffic, building a live inventory that updates automatically on every scan. The platform integrates with CI/CD pipelines and issue trackers to connect API discovery with active testing, ensuring security validation happens continuously. Its focus on deep business logic use cases, and has the best security testing engine in the market. It’s developer-first automation makes it one of the few tools blending discovery and dynamic testing within the same workflow.
Best for: Security and DevOps teams seeking continuous discovery tied to automated testing.
Pricing: Custom enterprise pricing.
Now operating under Akamai, Noname Security’s platform performs continuous API discovery across hybrid and multi-cloud infrastructures. It detects APIs through traffic analysis and gateway integrations while classifying endpoints based on exposure and sensitivity. Combined with Akamai’s network telemetry, it gives enterprises complete visibility into both internal and internet-facing APIs. Its strength lies in large-scale deployments that require unified discovery and runtime protection across distributed systems.
Best for: Enterprises managing large API ecosystems across hybrid or cloud environments.
Pricing: Custom. Need to contact Akamai for a quote.

Salt Security discovers APIs in real time using traffic inspection and behavioral analytics. The platform learns how APIs are used, identifies undocumented or deprecated endpoints, and ranks exposure risk based on activity and sensitivity. It also integrates with API gateways and SIEM platforms to enrich incident response workflows with runtime insights. By combining deep behavioral context with continuous monitoring, Salt gives teams an operational view of API behavior rarely achieved through static scans alone.
Best for: Organizations requiring runtime discovery and behavioral context for API security.
Pricing: Enterprise plan listed on AWS Marketplace (~$100,000 per year for 100M API calls).
Traceable AI combines code-level context with runtime visibility to map all APIs and their data flows across complex applications. Its hybrid approach merges gateway integrations, network traffic analysis, and machine learning to detect unmanaged or high-risk endpoints. The platform provides deep tracing for microservices environments and offers attack analytics that connect discovery findings to threat behavior. Traceable’s contextual intelligence allows teams to correlate discovered APIs with actual usage and security posture.
Best for: Teams operating in large-scale cloud-native or microservices environments.
Pricing: On AWS Marketplace, Traceable AI lists a discovery tier of 250 API endpoints at $20,000/year and a protection tier of 50 million API calls/month at US $70,000/year. Pricing is generally custom-quoted based on scale and features.
APIsec combines discovery with automated security testing through gateway integrations and external scanning. It identifies all public-facing and internal APIs, generates specifications for undocumented endpoints, and performs continuous validation using AI-driven test cases. The tool excels in automated coverage and remediation workflows that integrate directly into CI/CD pipelines. Its focus on automation makes it a strong fit for DevSecOps-driven environments.
Best for: Security teams automating discovery and penetration testing at scale.
Pricing: Custom enterprise pricing.
Tinfoil Security, acquired by Synopsys, extends API scanning and discovery within the Synopsys Software Integrity Suite. It identifies endpoints through OpenAPI specifications and dynamic testing, generating visibility across integrated applications. The solution focuses on integrating discovery with DAST workflows, enabling consistent security testing across APIs and web assets. For enterprises already relying on Synopsys tools, Tinfoil ensures continuity between API inventory and broader application security.
Best for: Enterprises using Synopsys for unified application and API security testing.
Pricing: Custom enterprise pricing.

After being acquired by F5 in 2024, Wib’s technology became part of the F5 Distributed Cloud API Security platform. It performs discovery through traffic monitoring, API gateway data, and schema validation, mapping each endpoint and detecting unmanaged APIs. Wib’s native integration with F5’s cloud network and WAAP services enhances its ability to detect and protect APIs in production. The combined platform now supports API risk scoring, data flow tracking, and automated protection.
Best for: Organizations that use F5 for application delivery and API protection.
Pricing: Usage-based model under F5 contracts; quote required.
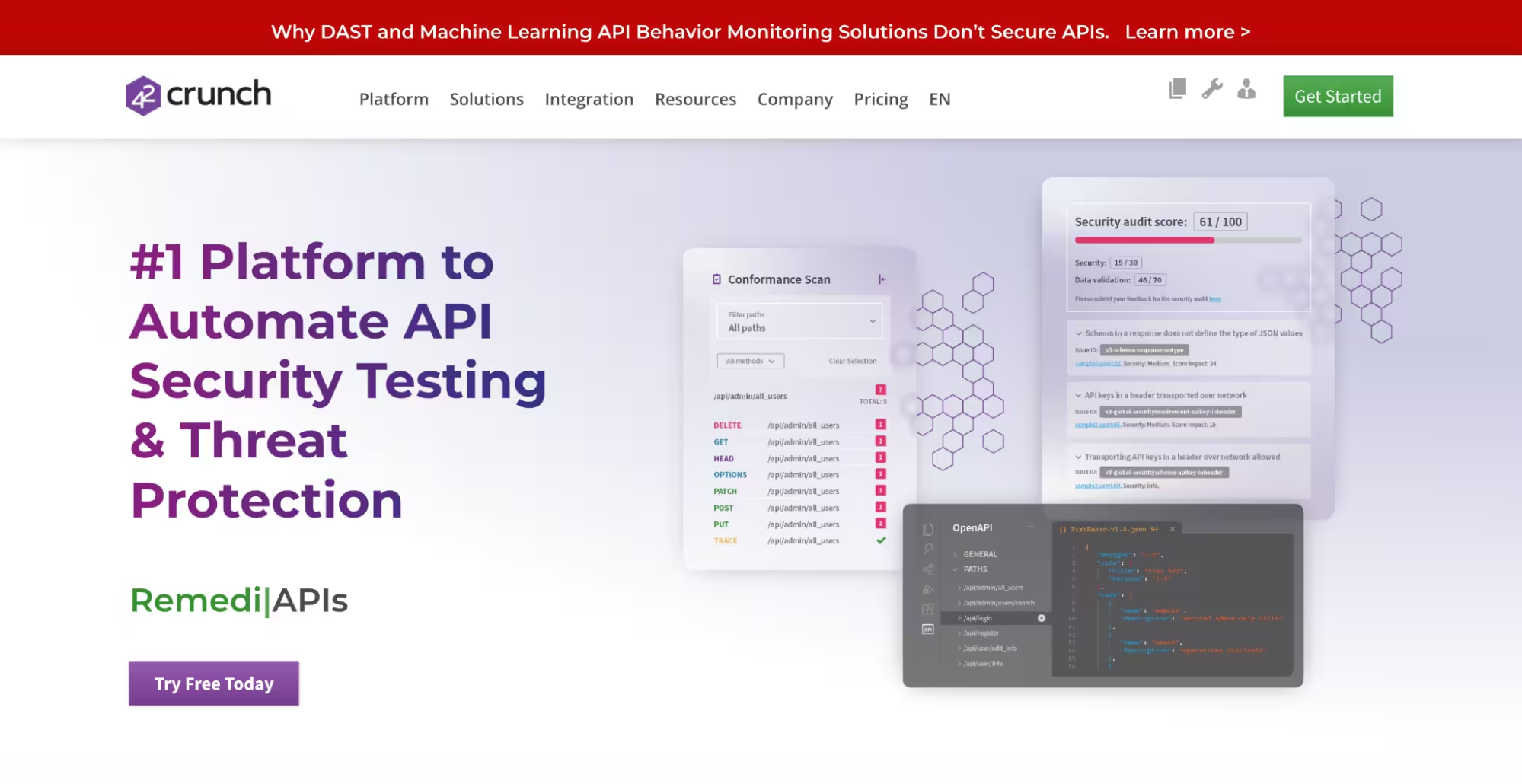
42Crunch focuses on design-time API discovery by importing and auditing OpenAPI specifications. It automatically validates specifications against compliance frameworks, highlights configuration errors, and maintains an API catalog that evolves in tandem with development. Its integration with IDEs and CI/CD tools helps teams detect issues before deployment. 42Crunch’s contract-based approach is particularly valuable for organizations prioritizing governance and compliance-driven security.
Best for: Teams focused on secure API design and documentation-driven governance.
Pricing: Free tier for single user; paid plans from ~$15/month.
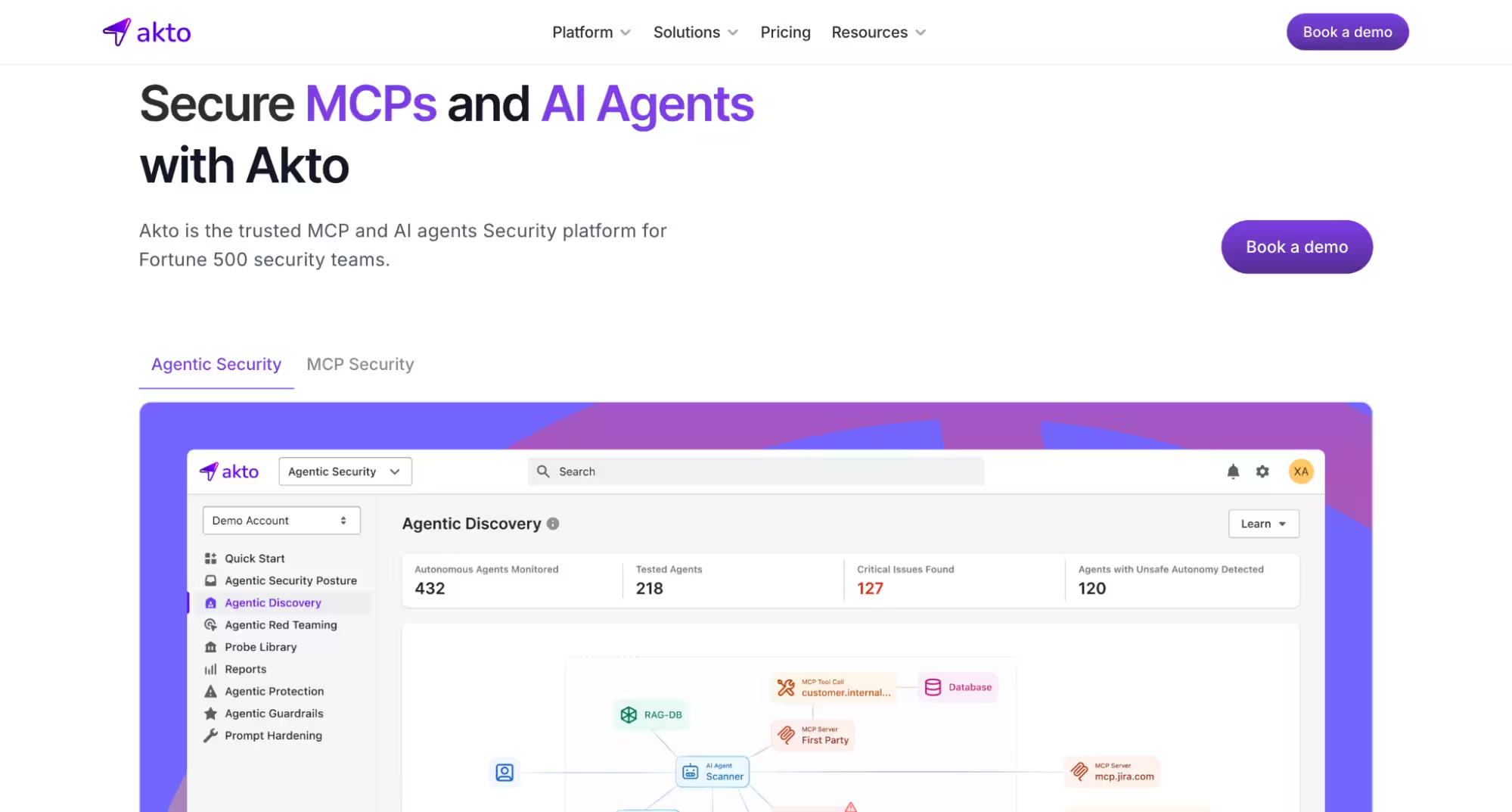
Akto offers a platform for API discovery and security. It scans code repositories, traffic logs, and cloud environments to identify APIs, classify them by risk, and test for compliance with OWASP API Top 10 categories. The tool includes open-source components, making it accessible to smaller teams, while its commercial version adds advanced automation and coverage visualization. Akto’s integration with CI/CD tools simplifies discovery without interrupting developer workflows.
Best for: Small to midsize teams needing affordable, automated discovery and testing.
Pricing: Free tier available; Professional plan around $1,890/month for 500 API endpoints (as of Oct 2025).
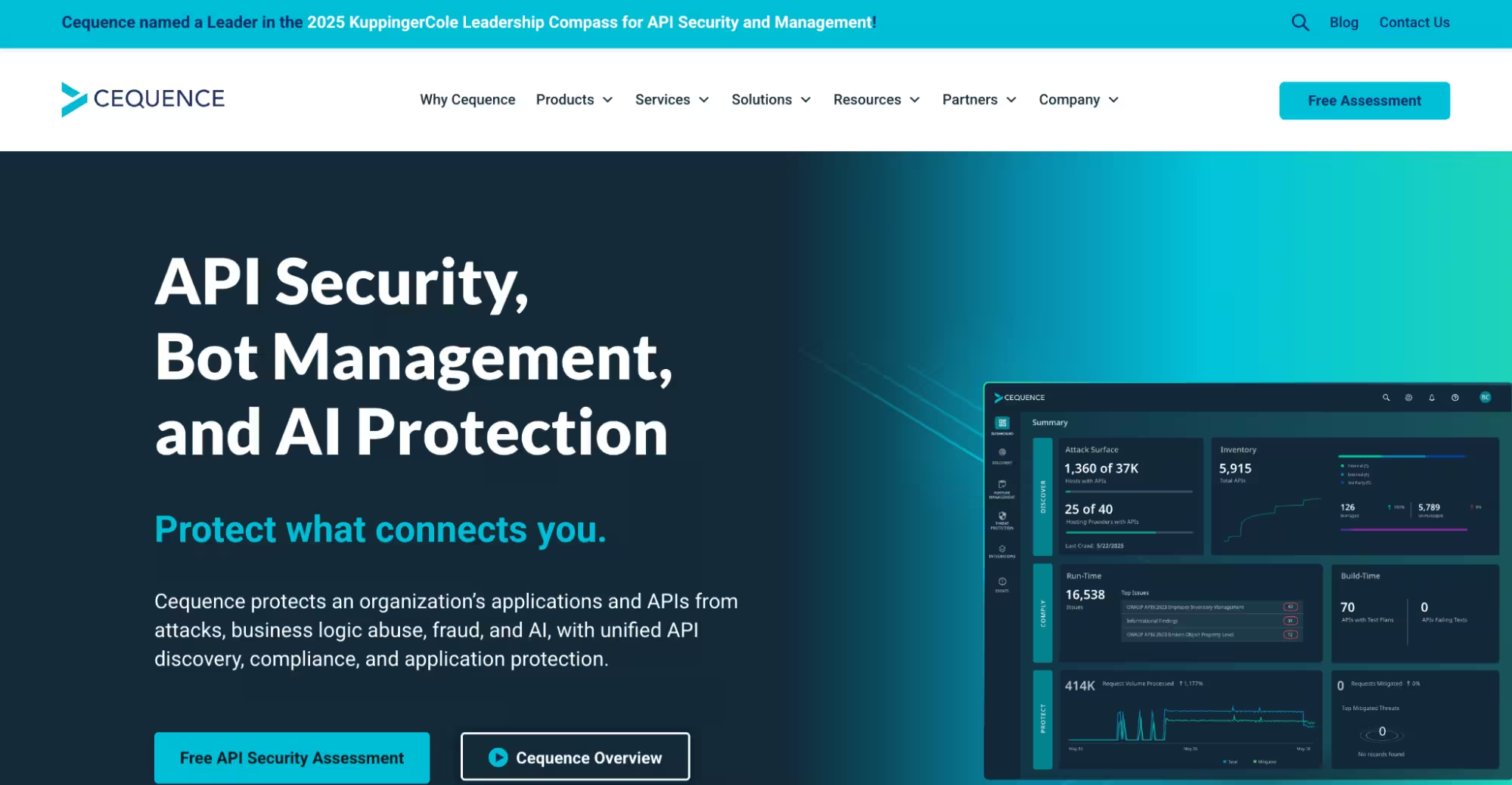
Cequence Security discovers APIs in real time through application traffic analysis and policy enforcement. It detects unknown, unmanaged, or third-party APIs, classifies them by sensitivity and exposure, and can automatically generate OpenAPI specifications for undocumented endpoints. Its runtime discovery pairs with behavioral analytics to detect anomalies and prevent abuse. Cequence stands out for its visibility into large-scale enterprise API ecosystems.
Best for: Enterprises prioritizing continuous, runtime discovery and API risk assessment.
Pricing: Custom enterprise quote.
Each tool approaches discovery differently, depending on how it integrates into development and production workflows. The table below summarizes deployment models, discovery methods, and ideal use cases to help teams choose the platform that aligns best with their environment:
Modern API discovery platforms must go beyond surface scans to deliver complete, continuously updated visibility. The best tools automate detection, learn from live traffic, and adapt intelligently as applications evolve.
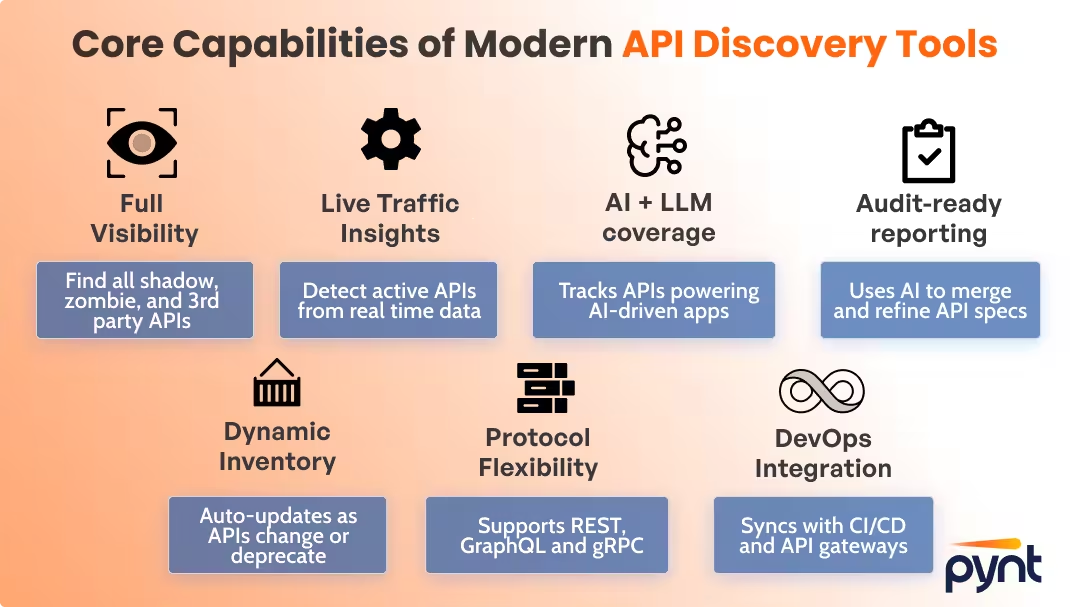
Choosing the right API discovery platform depends on your organization’s size, architecture, and development model. The best tools provide accuracy, automation, and scalability without disrupting developer workflows.
It’s not an exaggeration to say that API discovery has evolved from a technical necessity into a strategic capability that shapes how organizations build and secure digital ecosystems. It no longer serves only to locate endpoints but to create continuous awareness of how data moves, how services connect, and how change influences business operations.
As APIs continue to expand through AI integration and global cloud architectures, discovery will remain central to governance, compliance, and innovation. The next phase involves platforms that combine automation with intelligence, providing teams not only with visibility into their APIs but also with a deeper understanding of their purpose and behavior across the entire software lifecycle.
Discovery is the ongoing process of finding APIs; inventory is the catalog you maintain.
Learn more about API discovery fundamentals.
They compare observed traffic against documented endpoints to find gaps.
Understand shadow API risks and detection methods.
Yes. Modern platforms hook into your existing development workflow automatically.
See available integrations for your stack.
Pynt runs discovery and testing as one continuous workflow, not separate steps.
Explore API security testing capabilities.
Pricing varies wildly based on scale, features, and how vendors structure costs.
Compare automated discovery deployment options.
Yes. Gateways only see traffic routed through them—not your entire infrastructure.
Learn about API inventory best practices.
Initial findings surface within 24-48 hours; real value depends on workflow integration.
Understand shift-left security implementation timelines.
