The Shift Left paradox: 97% have tools, 35% drown in false positives, half of non-implementers won't even try
Pynt's latest research surveyed 250 security and engineering professionals across North America, the UK, and Germany to understand how organizations are implementing Shift Left security. While nearly half claim success, the data reveals a different story: widespread tool adoption coupled with execution failures, developer burnout, and a growing disconnect between security teams and engineering.
The study exposes how Shift Left, the practice of moving security earlier in the development lifecycle, has become a checkbox exercise for many organizations. Teams deploy tools but can't operationalize them. Developers drown in vulnerability alerts while security teams push for more coverage. As organizations race to "shift left," they're discovering that without proper workflows and team alignment, they're just shifting problems, not solving them.
Inside Our Research
This research is based on a survey conducted among 250 professionals across various industries, functions, and company sizes. The participants were specifically from technical and security-oriented roles:
- 29% InfoSec/AppSec professionals
- 28% Developers/Engineers
- 27% CISO/CIO/Head of Security
- 9% DevOps/DevSecOps
- 7% CTOs
The geographic distribution included 38% from North America, 30% from the United Kingdom, 27% from Germany, and 5% from other regions. Company sizes ranged from 100 to over 5000 employees, ensuring diverse organizational perspectives.
Key Findings
- Half of companies claim they've "Shifted Left" but most admit execution is failing.
47% of the 250 surveyed security and engineering professionals say their organizations have implemented Shift Left, yet many still face execution gaps and security inefficiencies. - False positives are killing Shift Left with 35% of teams wasting cycles on noise.
35% of security and engineering professionals cite false positives as their biggest challenge, creating alert fatigue across both security teams and developers. - 31% of teams can't integrate security tools into developer workflows.
Integration issues are the second-biggest roadblock, with security tools clashing against existing development processes rather than embedding smoothly. - One in four developers report drowning in vulnerability alerts beyond just false positives.
25% of respondents say developers are overloaded with the sheer volume of vulnerabilities flagged, even when the alerts are legitimate issues that need fixing. - Security Champions work but adoption is lopsided: 75% in Europe vs. 50% in the U.S.
67% of organizations have Security Champions embedded in engineering or QA teams, with European companies leading adoption compared to American firms. - 97% of surveyed organizations have the tools but can't make them work.
Nearly all respondents have implemented SAST, DAST, or SCA tools, yet the same companies report false positives, integration failures, and developer overload as top problems. - The developer-security split: 65% want to fix code while 42% of CISOs prefer WAF blocks.
When facing internet-facing flaws, most respondents prefer fixing bugs in code, but security leaders are more likely to block issues at the edge with WAF rules (42% vs. 33% overall).
Shift Left Adoption: The Reality Gap
Tool adoption tells one story. Execution tells another. From 250 professionals surveyed across the security and engineering ecosystem:
While 47% of organizations claim to have fully implemented Shift Left, a large portion are still in the process or have only partially implemented it. Of those who haven't implemented Shift Left, half of them have no plans to do so at all, showing a stark divide in adoption rates.
Regional differences amplify the divide: Germany and the UK show 52% implementation compared to 42% in the U.S. More tellingly, 36% of German organizations plan to implement soon versus just 20% of American firms.
Tools Everywhere, Success Nowhere
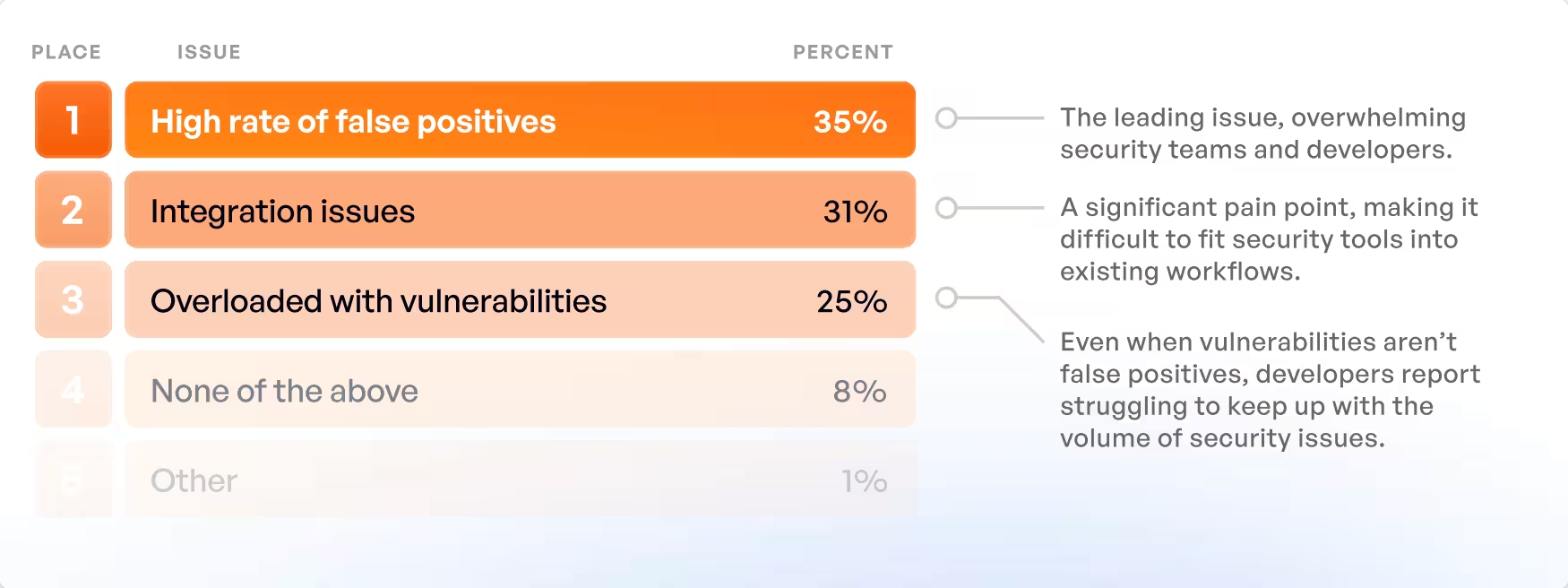
This is not a tooling problem. 97% of organizations have implemented security testing tools, with SAST dominating at 36%, SCA at 31%, and DAST at 29%. Yet these same organizations report three critical failures:
- High rate of false positives (35%): The leading issue, overwhelming security teams and developers
- Integration issues (31%): A significant pain point, making it difficult to fit security tools into existing workflows
- Overloaded with vulnerabilities (25%): Even when vulnerabilities aren't false positives, developers report struggling to keep up
The tools work. The processes don't.
The AI Acceleration Crisis
As AI and LLMs transform development velocity, the Shift Left dysfunction is accelerating. Traditional security tools weren't designed for the speed and scale of AI-generated code. Organizations now face a dual challenge: fixing existing Shift Left failures while adapting to AI-driven development that amplifies every existing problem.
The compositional risk in modular AI systems presents an entirely new threat vector. When just three AI components compose, 52% of systems become "high risk." When five or more components combine, that risk exceeds 70%. Th ese aren't vulnerabilities that traditional scanning can catch by simply running earlier in the pipeline.
AI isn't just changing how fast we code. It's changing what security needs to catch. And our current Shift Left approach is already failing without AI in the mix.
The Developer-Security Standoff
When facing an internet-facing security flaw, responses split along role lines:
- 65% want to fix the bug in code (doing it "right")
- 33% prefer blocking with WAF rules (doing it "fast")
- 2% choose "do nothing, not my problem" (the honest minority)
But drill into security leadership and the split deepens: 42% of CISOs prefer WAF blocks over code fixes. They'd rather contain than cure, revealing how delivery pressure trumps security ideals.
This isn't lazy thinking, it's systemic dysfunction. Developers see security as extra work. Security sees unfixed vulnerabilities as unacceptable risk. Both are right. Neither can win.
Security Champions: The Only Thing That Works
Organizations with Security Champions report markedly better outcomes. These embedded security advocates transform Shift Left from mandate to practice:
- 67% overall adoption but with massive regional variance
- 75% in European companies have champions driving change
- 50% in U.S. companies, a 25-point adoption gap
Champions work because they translate between worlds. They speak developer and understand security. They turn "you must fix this" into "here's how we fix this."
Given that so many organizations train security champions, embedding security testing in the testing process becomes much easier. Organizations can crush security bugs earlier, without relying on unmotivated developers. This approach could improve security posture and reduce friction between teams.
What's Next
To address the challenges of Shift Left adoption, organizations should consider these strategies:
- Embed Security into Testing: Relying solely on developers isn't working. Security testing should be part of the QA process
- Kill the false positive rate through tuned rules and context-aware scanning
- Automate Security Testing: Reduce friction by integrating automated security testing tools within CI/CD pipelines
- Prepare for AI-accelerated development: Traditional Shift Left tools weren't designed for the velocity and scale of AI-generated code. Organizations need context-aware, automated security that can keep pace with AI development speeds
- Invest in Security Champions to bridge the gap between developers, security teams, and testers
- Choose integration over coverage: fewer tools that work beats more tools that don't
Full Survey Data
The complete report includes all 250 responses, regional breakdowns by country, company size correlations, and the survey methodology.
The promise of Shift Left remains valid: fix problems early, ship safer code. But until organizations solve the workflow problem, they're just shifting problems left, not solving them. The 47% claiming success are mostly lying to themselves. The 49% of non-implementers with no plans might be the honest ones.



.svg)







