DAST vs SAST: Key Differences and Use Cases for Application Security Testing


.svg)

In practice, DAST and SAST are often misunderstood because their strengths and weaknesses reveal themselves only when applied to real development workflows. Static analysis is invaluable early in the lifecycle, where catching improper input validation or unsafe library calls can prevent technical debt from accumulating. Dynamic testing, on the other hand, becomes critical once an application is deployed, where server misconfigurations, broken access controls, and exposed APIs are only observable in a running system.
Neither method fully addresses modern API security challenges on its own, a gap I have repeatedly encountered when working with API-driven and microservice-based architectures. Understanding where each method excels and where it falls short is essential for building a security testing strategy that matches how applications are actually built and operated today.
Dynamic Application Security Testing (DAST) is a black-box testing methodology that identifies security issues in a running application without requiring access to its source code. It is designed to uncover risks such as Cross-Site Scripting (XSS), SQL Injection, and security misconfigurations. DAST is language-agnostic, making it suitable for applications built with any tech stack. It is especially relevant for assessing APIs, web frontend, and backend services during execution.
DAST operates by interacting with a running application through its exposed interfaces, typically over HTTP. It sends crafted inputs to simulate real-world attacks and observes the application's responses to detect abnormal or insecure behavior.
The process involves crawling the application to discover accessible endpoints, injecting test payloads, and analyzing outputs for evidence of flaws such as authentication issues, improper input handling, or sensitive data exposure. Since DAST does not analyze static code, it focuses entirely on behavior observed during execution. This makes it well-suited for identifying runtime issues that are invisible during static analysis.
DAST reveals security flaws that only appear when an application is running. It uncovers issues missed by static analysis, such as insecure server configurations, runtime authorization gaps, and logic flaws in exposed endpoints. Since it tests actual behavior over HTTP, DAST provides insight into how an attacker might exploit the system in a production environment. This makes it essential for evaluating real-world risk, especially for web apps and APIs.
Static Application Security Testing (SAST) is a white-box testing methodology that examines an application’s source code or compiled artifacts without running the application. It helps detect security flaws such as buffer overflows, weak encryption, and improper input handling at the code level. SAST is typically applied early in the software development lifecycle, allowing developers to identify and remediate issues before deployment. It is language-specific and best suited for detecting weaknesses in code structure, logic, and insecure coding practices.
SAST scans an application’s source code, bytecode, or binaries without executing them. It identifies insecure patterns by matching code against predefined rules and known vulnerability signatures. The process typically runs during development or build phases, enabling early detection of flaws. Since SAST analyzes the internal logic and structure of the code, it can pinpoint issues like data flow problems, insecure function usage, and violations of secure coding standards.
SAST enables developers to detect and fix security flaws early in the development process, before code is compiled or deployed. This reduces the cost of remediation and improves overall code quality. Because SAST provides full visibility into the application’s internal structure, it can catch deep logic errors, unsafe coding patterns, and misuse of sensitive libraries. It also supports compliance by enforcing secure coding practices across the codebase.
SAST is performed early in the development lifecycle, even before the code is compiled. It involves analyzing the source code, byte code, or application binaries to identify vulnerabilities. This allows developers to detect and fix vulnerabilities early in the development process, which can save time and resources.
On the other hand, DAST is performed after the application has been developed and is in its running state. It involves testing the application from the outside and simulating the actions of an attacker to find vulnerabilities. The advantage of DAST is that it can identify vulnerabilities that are only visible when the application is running, including those that may have been missed during the SAST stage.
SAST focuses on the internal structure of the application, examining the source code, design, and architecture to find potential vulnerabilities. It's a thorough and meticulous process that can detect a wide range of vulnerabilities, from input validation issues to buffer overflows.
On the other hand, DAST focuses on the external behavior of the application. It tests the application's interfaces, HTTP and HTML interfaces, server-side scripts, and more to find vulnerabilities that can be exploited by attackers.
SAST can identify vulnerabilities related to the code and architecture of the application, such as insecure coding practices, use of insecure libraries, and buffer overflows. It's also capable of detecting vulnerabilities in the early stages of development, making it an invaluable tool for developers.
DAST excels at detecting vulnerabilities that are only visible when the application is running. This includes vulnerabilities related to the runtime environment, such as insecure server configurations, vulnerabilities in third-party components, and flaws in the application's interaction with other systems.
SAST provides a deep, thorough analysis of the application's code and architecture, but it may not cover all the possible runtime scenarios. It's excellent for identifying vulnerabilities in the code, but it may not detect all the vulnerabilities that can be exploited at runtime.
DAST provides a broad, surface-level analysis of the application's behavior at runtime. It can detect a wide range of runtime vulnerabilities, but it may not provide as deep an analysis as SAST. It's excellent for identifying vulnerabilities that are visible at runtime, but it may not detect vulnerabilities in the code or architecture.
Application Programming Interfaces (APIs) are a prime target for attackers because of their accessibility and the sensitive data they handle.
SAST analyzes API source code for issues such as weak authentication logic, improper data validation, and unsafe coding patterns. Since it examines static code, it can uncover flaws in the API’s internal logic and how requests and responses are handled.
DAST evaluates APIs at runtime by sending crafted requests to live endpoints and observing responses. This approach reveals vulnerabilities that only manifest when the API is active, such as misconfigurations, improper error handling, and sensitive data exposure during transmission.
While both methods contribute to API security, they are not built for the API use case or protocol-level issues unique to APIs. This is why specialized API security testing tools like Pynt are essential for comprehensive coverage. Pynt enhances standard DAST with context-aware attacks, automatically generating and executing attack simulations against APIs, identifying misconfigurations, broken access controls, and sensitive data exposure across real-world runtime flows.
SAST requires integration into the development environment and access to source code, build artifacts, and language-specific analyzers. This setup can be complex, particularly in polyglot projects, and often involves configuring rulesets for each language. DAST has a much simpler setup, as it only needs a deployed, running application to begin testing, making it more accessible in environments where code is unavailable or proprietary.
Pynt simplifies DAST setup by requiring only access to a running API and documentation (like an OpenAPI spec). It automates discovery and testing, making it easy to use even in complex or microservice-based environments.
SAST tends to produce more false positives because it analyzes potential code paths that may not be reachable in production. This can overwhelm developers with findings that have little real-world impact. DAST generally yields fewer false positives since it validates only exploitable vulnerabilities observable during runtime. However, it can miss flaws buried deep in the code logic that are not externally exposed.
Pynt reduces false positives and blind spots by combining dynamic testing with contextual API behavior analysis, delivering a practical balance between DAST and IAST without needing source code.
SAST is highly effective at embedding security earlier in the SDLC, integrating into IDEs, pre-commit hooks, and CI/CD pipelines to catch issues before code is deployed. DAST integrates later in the cycle, running in staging or pre-production environments where it can assess the security posture of the deployed application without disrupting development workflows.
SAST is primarily used by developers, secure code reviewers, and AppSec engineers who have direct access to and understanding of the codebase. It supports developer-centric workflows. DAST is better suited for QA teams, penetration testers, and DevSecOps professionals who focus on validating application behavior under attack scenarios. Pynt specifically supports security teams and developers by automating API security testing throughout CI/CD workflows, even when code access is limited.
SAST is ideal for ensuring compliance with secure coding standards, detecting insecure functions, and preventing the introduction of risky patterns early in development. DAST is more appropriate for runtime risk assessment, testing exposed endpoints for misconfigurations or broken access controls, and validating the security of APIs and web services as deployed.
SAST analyzes static files such as source code or binaries without executing the application, making it suitable for early-phase checks. DAST requires the application to be fully deployed and operational, as it probes the system by sending crafted requests and observing responses during execution.
SAST needs access to the full source code, which can limit its use when dealing with third-party or closed-source components. DAST does not require any code access, enabling black-box assessments of proprietary, external, or cloud-hosted applications where internal code cannot be inspected.
SAST depends on analyzers and rulesets that are specific to each programming language and framework used in the application. Multilingual projects may need multiple analyzers configured properly. DAST, in contrast, is language-agnostic because it interacts with the application through its exposed interfaces, making it equally applicable to any technology stack.
While both SAST and DAST are widely used for application security testing, each has unique strengths and limitations. Traditional DAST tools often fall short in modern, API-centric architectures, which is where DAST 2.0, like Pynt, fills the gap. The comparison below highlights the trade-offs and improvements across these three approaches to help teams choose the right solution for their security and development workflows:
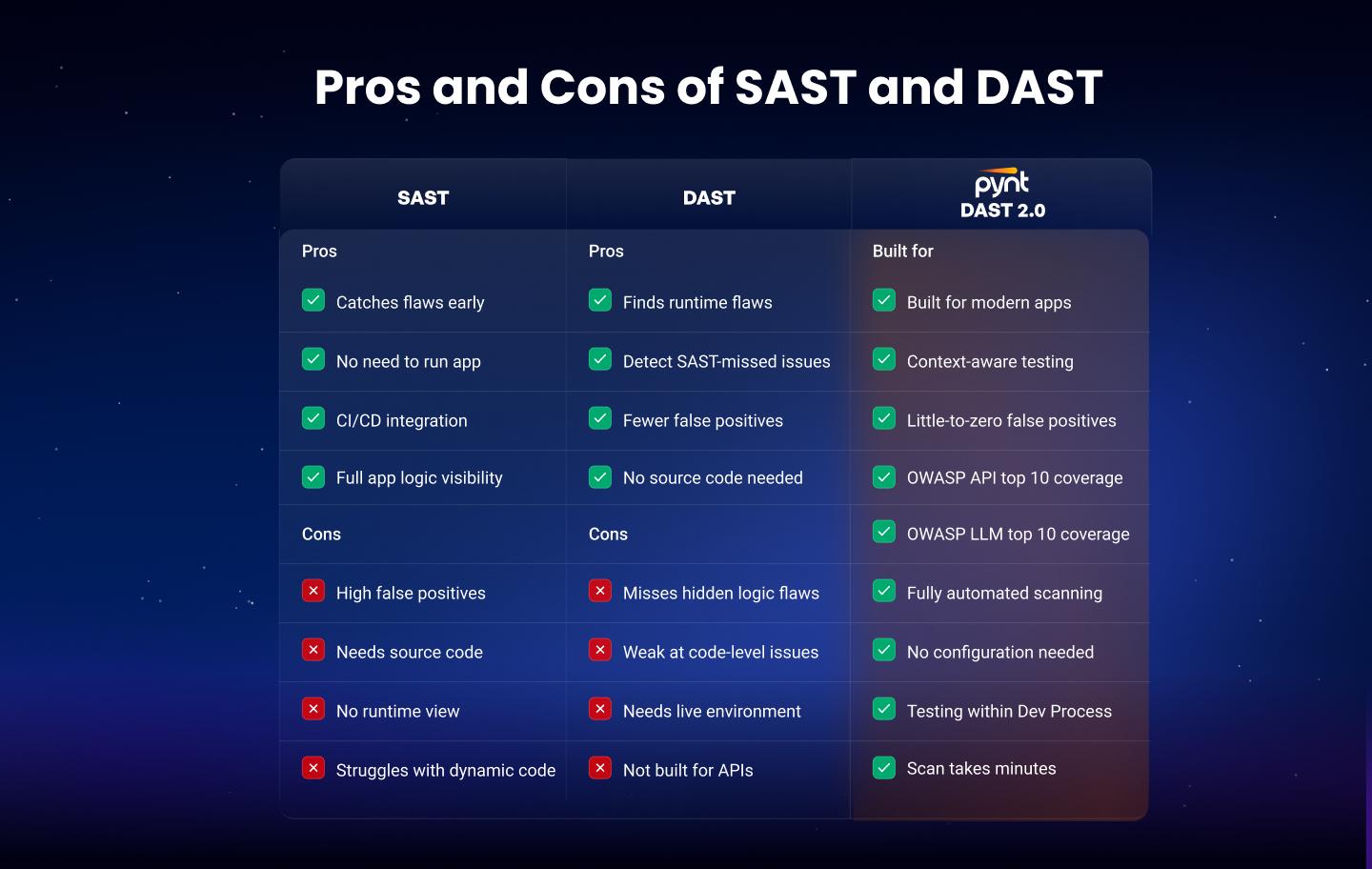
SAST and DAST tools vary in capabilities, integrations, and ideal use cases. Below are commonly adopted tools that support security testing across different stages of the development lifecycle.
Each security testing method fits specific stages and objectives within the software development lifecycle. Depending on the application's architecture, risk tolerance, and development maturity, teams may use SAST, DAST, or both for layered protection.

Pynt, unlike traditional Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) tools, offers a specialized and comprehensive approach to API security testing. While SAST and DAST tools may provide some support for APIs, they often lack the depth and specificity required to address the unique challenges of modern, distributed architectures. Pynt is purpose-built to excel in this domain.
One of the key distinctions of Pynt is its focus on analyzing response payloads rather than scanning source code. Traditional SAST tools examine the source code for risky patterns, while DAST tests APIs in their operational state. Pynt goes further by understanding the real behavior of APIs through their responses, uncovering vulnerabilities invisible to static and runtime analysis.
Pynt also adapts seamlessly to a variety of API architectures, authentication methods, and data formats, making it effective across diverse environments. Its unique capabilities include:
These features make Pynt a valuable addition to any API security testing toolkit, addressing the limitations of traditional SAST and DAST tools while enabling faster, more accurate detection of real-world risks. Learn more about how Pynt can overcome the unique API security testing challenges.
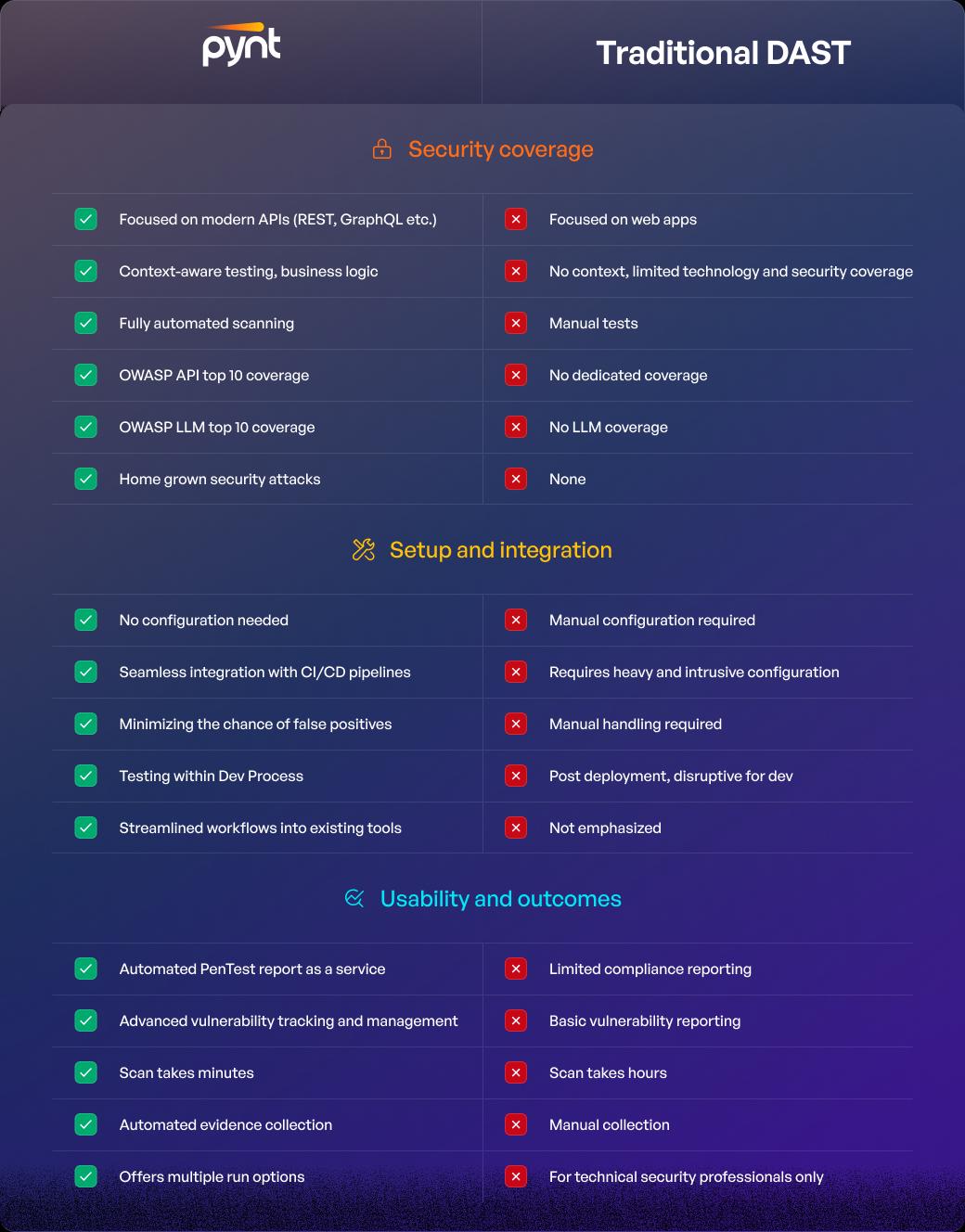
SAST and DAST serve distinct but complementary purposes in modern application security testing. SAST excels at catching insecure code patterns before deployment, helping teams remediate issues early in the software development lifecycle. DAST provides visibility into runtime behavior, uncovering security flaws that only emerge when the application is operational. Relying on one without the other leaves significant gaps in your security posture.
A combined approach delivers layered protection, from enforcing secure coding practices to validating real-world execution paths. For organizations building or maintaining API-first architectures, tools like Pynt enhance coverage by automating context-aware, runtime testing across critical interfaces, effectively identifying vulnerabilities that traditional methods might overlook. Integrating SAST and DAST within a unified DevSecOps pipeline isn’t just best practice but a baseline for securing today’s complex, distributed applications.
Traditional DAST doesn't focus on the API problem and can’t handle complex B2B API use cases. Those tools lack context, require manual work and heavy configuration. Pynt detects automatically and continuously API vulnerabilities in the wild.
Not exactly. While both analyze applications from the outside, DAST goes beyond automated scans by simulating attacks against a live system. It actively interacts with the application to uncover issues like logic flaws or misconfigurations that basic scanners might overlook.
Yes. Using both methods provides broader coverage across the software development lifecycle. SAST catches code-level issues early, while DAST identifies runtime risks during execution. Together, they help reduce blind spots and improve overall application security.
DAST is typically more effective for API security testing because it evaluates how APIs behave in real-world conditions. It identifies issues such as:
Yes, both approaches align well with modern development workflows. SAST integrates into CI/CD pipelines for early detection, while DAST fits into staging or post-deployment phases. Used together, they support continuous security without slowing down releases.
Each approach focuses on different layers:
SAST depends on the programming language and requires specialized analyzers for each one. DAST, on the other hand, is language-agnostic and evaluates applications through their external behavior, making it applicable across tech stacks.
Learn more about DAST & Application Security Testing with these resources:
