What Are Business Logic Vulnerabilities & How to Prevent Them


.svg)

Business logic vulnerabilities arise when attackers manipulate the intended behavior of an application to achieve outcomes that were never designed or approved. These flaws occur in the business logic layer, where assumptions about user behavior drive workflows like payments, discounts, approvals, or account actions. If those assumptions are incorrect or incomplete, the system can be pushed into a state where normal features are abused to bypass controls or trigger actions out of order.
In my experience working across application security and API testing, these gaps are rarely caught by scanners or standard checks. They require a deeper understanding of how logic flows across the system and how legitimate users might stretch those flows in unexpected ways. The only way to catch them early is to model logic from the start, test abuse paths intentionally, and treat business processes as attack surfaces, not just features.
Business logic vulnerabilities affect the way an application processes decisions, workflows, or rules in its business logic layer. They emerge when the system makes incorrect assumptions about how users will interact with it. Attackers take advantage of these blind spots to perform valid actions with unintended consequences, often without triggering alerts or breaking any rules in the code.
While traditional flaws involve broken code or misconfigurations, business logic vulnerabilities result from incorrect assumptions baked into the application's processes. The table below outlines the key differences between the two.
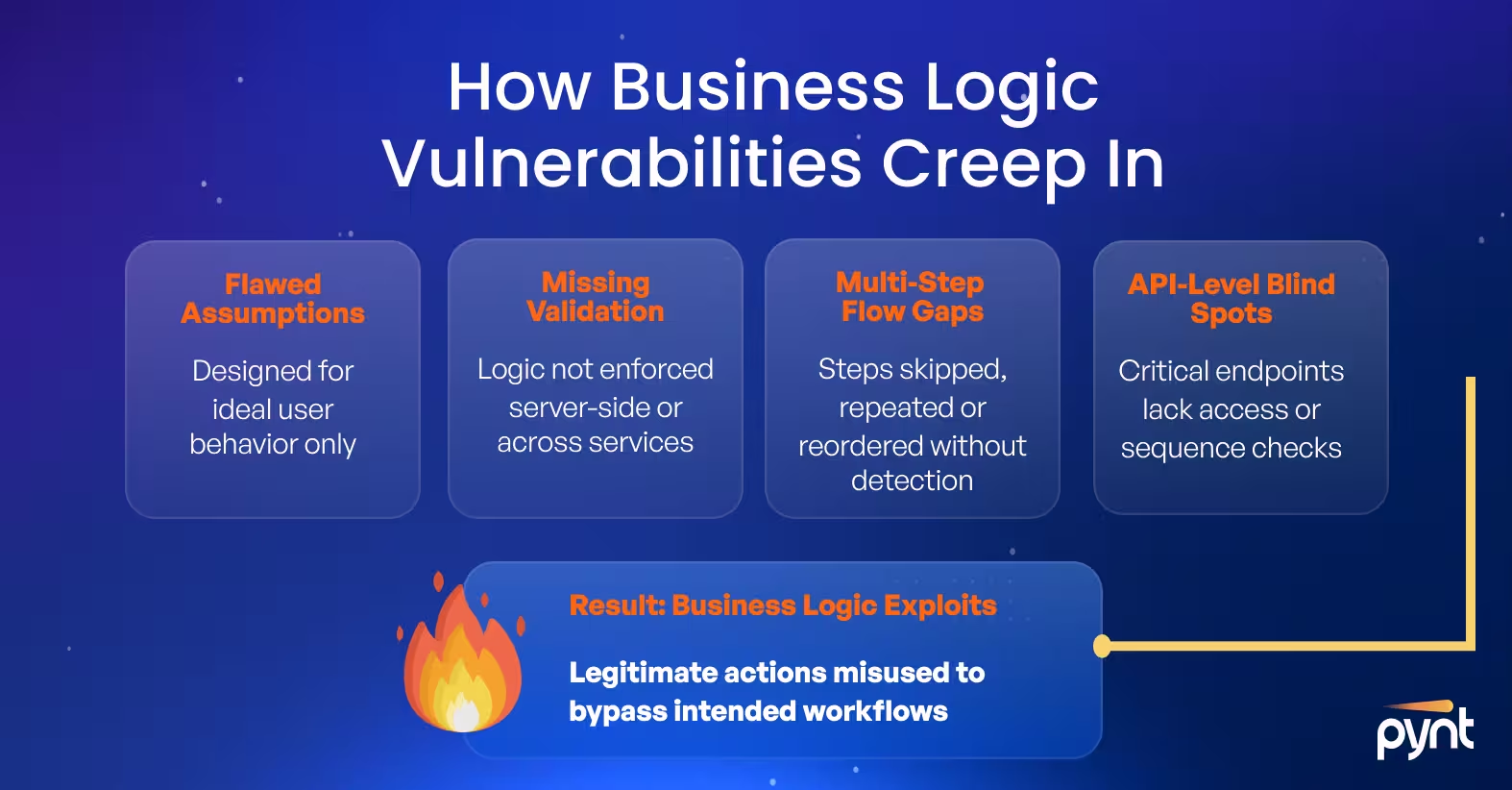
Business logic vulnerabilities emerge when developers make incorrect assumptions about user behavior or fail to enforce rules across workflows. These flaws often stem from gaps in validation, unclear process boundaries, or unexpected sequences of actions that the system accepts as valid.
For example, an application might assume users will follow a specific order of steps. An attacker who skips, repeats, or reorders those steps could gain access to restricted actions or bypass internal checks. Logic flaws can also surface when different parts of a system, such as APIs or microservices, handle related processes inconsistently.
The growing complexity of applications, especially those using third-party integrations, increases the risk. Security controls applied in one layer may be ignored or misaligned in another, leaving logic gaps that are difficult to catch without end-to-end abuse case testing.
Business logic vulnerabilities can have significant impacts on an organization, its applications, and its users. The consequences of exploiting these vulnerabilities vary depending on the nature of the application and the data it handles, but they often include:
Business logic vulnerabilities appear in many forms, often tied to how a system expects users to behave. Τhey reflect gaps between what the business intended and what the application allows. Below are common categories where these flaws emerge, along with examples that show how misuse of logic can result in unintended outcomes.
Applications that rely on the frontend to enforce rules expose critical gaps in logic. Attackers can manipulate browser behavior, modify client-side code, or intercept requests to bypass restrictions entirely. Features like read-only fields, JavaScript-based validations, or disabled buttons can all be ignored or altered by users acting outside the intended flow.
To address this, all logic and validation that governs access, pricing, and user actions must be enforced on the server. The frontend should never be trusted to decide what a user is allowed to do.
When applications are built around rigid expectations of how users behave, logic flaws emerge. Attackers explore what happens when they take actions out of order, repeat steps, or skip critical transitions. These edge cases are rarely tested in typical QA cycles but often lead to real impact.
For example, a user might apply a discount code, remove items from the cart, and retain the discount on cheaper products. This sequence is valid from the system’s perspective but produces an unintended result. These issues arise because the application assumes users will follow a narrow, predefined path.
Some logic flaws depend entirely on the domain where the application operates. These are not generic issues. They require knowledge of how the business works and how its rules can be manipulated.
Detecting these flaws means testing from the perspective of someone who understands how the system is meant to operate, and how it could be pushed outside of those bounds.
This OWASP API Top 10 item highlights a common logic flaw: APIs exposing critical operations without verifying the context of access. These business logic vulnerabilities allow users to invoke powerful backend actions simply because the endpoint exists, and no check is in place to confirm who should be using it.
A user might replay previous API calls, change request parameters, or elevate privileges by calling undocumented or internal endpoints. These flaws are especially dangerous in systems that use APIs for both frontend interactions and administrative tasks, without fully separating the logic for each.
Business logic vulnerabilities can take many forms, but most fall into identifiable categories based on how attackers misuse the application’s expected behavior. The table below outlines key types of logic flaws, how they work, and the kinds of impact they can have in real environments.
Business logic vulnerabilities have led to serious financial loss, reputational damage, and large-scale fraud. The following cases show how attackers exploited application logic to bypass intended workflows or trigger unauthorized outcomes. Each one highlights a specific failure in business logic and what organizations can learn from it.
Attackers found that Uber’s referral program did not validate whether referrals were genuine. By creating fake accounts and cycling through referral codes, they repeatedly earned credits without referring to real users.
Lesson learned: Systems involving rewards or payments must verify behavior through traceable actions, not just user-submitted data. Logic tied to incentives must be tested for abuse scenarios.
In multiple cases, travelers discovered they could book cheaper tickets by skipping segments of multi-city flights. Airline pricing engines calculated costs based on route combinations but did not enforce full completion of each leg.
Lesson learned: Business processes that assume a specific sequence of user behavior must include validation of real-world usage. Logic should be reinforced at each step, not just at booking time.
A researcher reported that Shopify’s gift card endpoints lacked limits and did not enforce business logic around issuance or redemption. By sending automated requests, they could identify valid codes and access funds.
Lesson learned: Inputs that appear technically valid can still break business logic if rules around frequency, access scope, and sequencing are missing. API security requires logic awareness, not just functional correctness.
Business logic flaws can’t be spotted by looking at broken inputs or error messages. They live in the design of workflows and the assumptions behind user actions. Identifying and testing them means stepping into the mindset of someone looking to manipulate the system through legitimate behavior.
To identify logic flaws, look for areas where the application assumes users will behave in specific ways. These include approval flows, discount applications, multi-step processes, or role transitions. Any area with conditional logic or hidden business rules is a candidate.
Key indicators:
Testing for these flaws involves simulating real user behavior in unexpected ways. The goal is to stay within the rules of the application while producing outcomes that violate business intent.
Effective testing strategies:
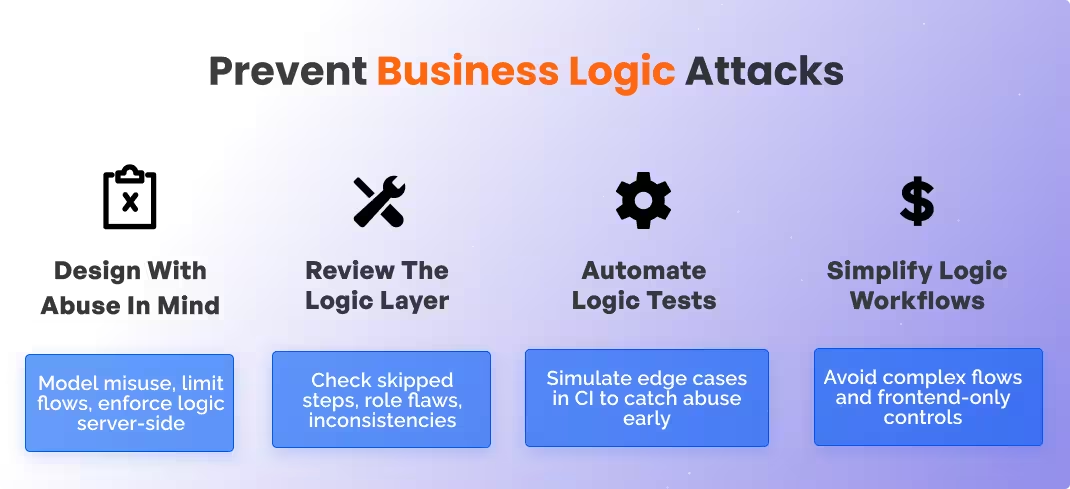
Preventing logic flaws begins with treating business workflows as part of your threat model. These issues often stem from flawed assumptions in how users interact with systems. The following practices reduce risk during design, implementation, and ongoing development.
Secure logic starts during planning. Teams need to anticipate how real users might stretch or break the expected behavior of workflows.
Code reviews must go beyond technical correctness and examine how decisions are made and enforced in business flows.
While many logic flaws are manual in nature, teams can still automate certain forms of testing to detect misuse or regressions.
The more complicated the logic, the easier it becomes for attackers to find blind spots. Simpler workflows make testing and maintenance more effective.
While no single tool can detect every business logic flaw, the right combination of technologies can help identify weak points, simulate abuse cases, and monitor for unexpected behavior.
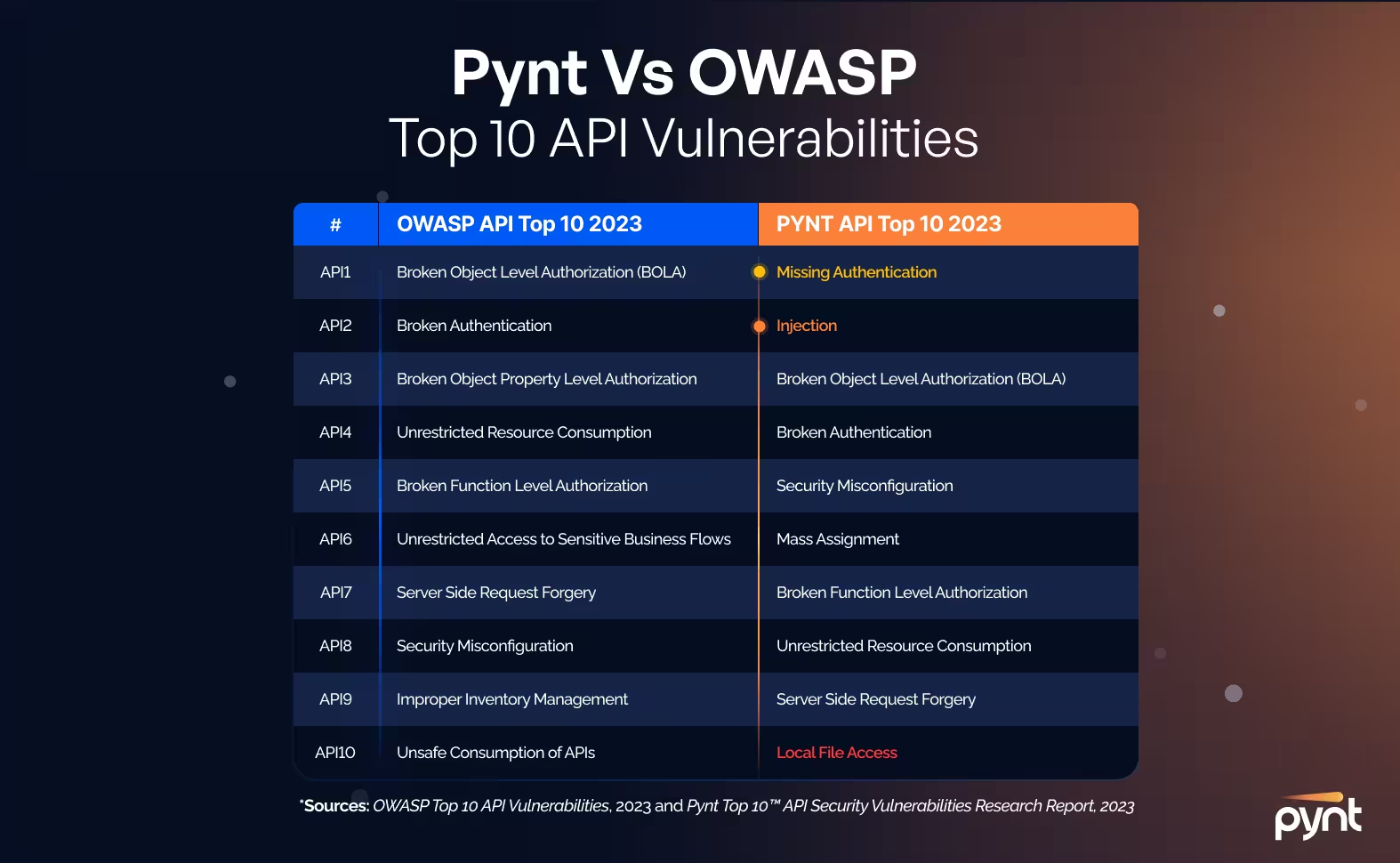
Protecting your APIs against OWASP Top 10, API business logic vulnerabilities included, through API security testing is critical in the threat climate of 2024. 'Shifting-left', and focusing your efforts on early discovery and resolution of vulnerabilities is proven to be the most effective way to handle such vulnerabilities. This proactive stance in the software development life cycle allows for:
These aspects collectively enhance the overall security posture by addressing API vulnerabilities at their inception, rather than as an afterthought.
Business logic vulnerabilities are among the most difficult issues to detect because they live in assumptions, not broken code. They exploit how a system is supposed to behave and not how it fails. Preventing them requires thinking like a user who wants to win by bending the rules. That means modeling abuse paths early, testing workflows beyond their ideal paths, and reinforcing logic controls at every layer. With the right mindset, testing strategy, and tooling, organizations can close the logic gaps that attackers depend on.
Because they exploit assumptions in workflows rather than broken code, developers often build processes around expected user behavior without accounting for edge cases or abuse paths. These flaws aren’t flagged by scanners or standard tests, so they persist unless specifically tested for.
Technical vulnerabilities stem from code errors, such as input validation failures or insecure configurations. Logical vulnerabilities arise when business processes behave in unintended ways due to flawed assumptions, allowing valid actions to produce unintended results.
Business logic defines how applications handle critical operations like approvals, transactions, and user roles. If that logic can be manipulated, attackers can bypass controls or gain unauthorized outcomes without breaching traditional security mechanisms.
Application logic governs how software functions at a technical level, like data processing or UI rendering. Business logic handles domain-specific decisions, such as pricing rules, workflow conditions, or role-based actions tied to real-world operations.
These are attacks where users exploit valid features in unintended ways to manipulate workflows. Common examples include bypassing approval steps, misusing discount logic, or triggering backend functions through direct API calls.
They require a deep understanding of how the system is supposed to work and how it might be stretched. Standard testing misses them because the behavior is technically valid. Addressing them means thinking like an attacker and building abuse-case testing into development.
Learn more about API vulnerabilities and security misconfigurations with these resources:
