Pynt’s latest research analyzes 281 MCP configurations collected from open agent frameworks and plugin stacks. MCPs act as the connectors between AI agents and the APIs, tools, or execution environments they control. While each plugin may seem safe on its own, an innocent combination can create invisible attack surfaces that bypass traditional security checks.
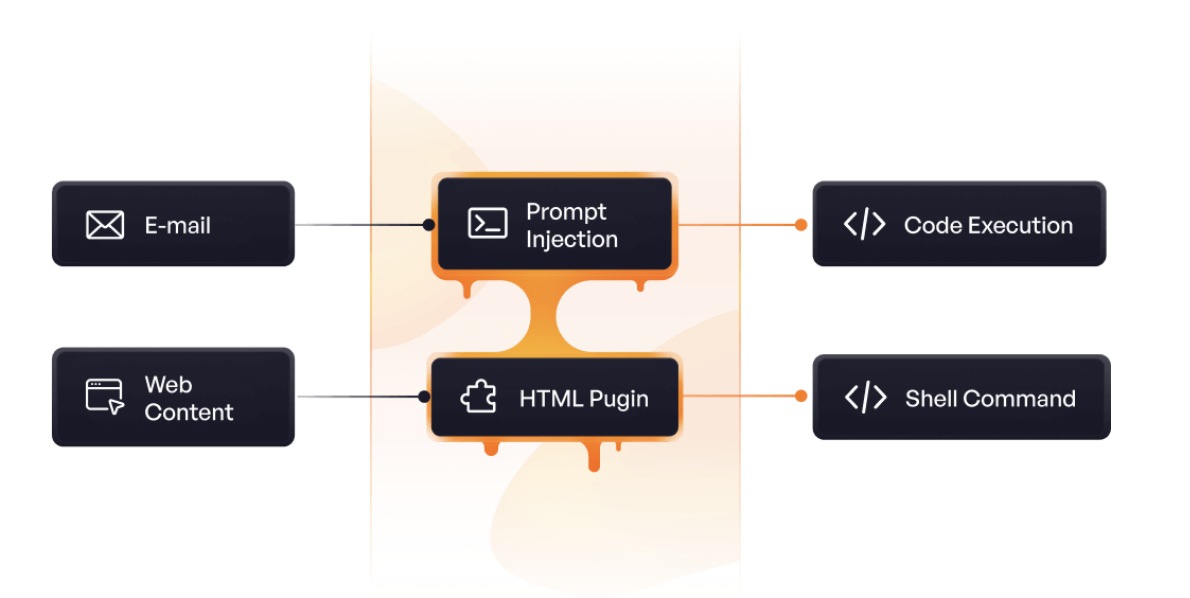
The study focuses on how untrusted inputs and privileged actions intersect in real-world systems. In several live cases, a single crafted Slack message or email triggered background code execution with zero human involvement. As MCPs evolve into the execution layer of modern software, their risks now match or exceed those of traditional APIs, but the attacks are faster, quieter, and harder to detect.
Key Findings
- More than 7 in 10 MCP plugins expose powerful actions that attackers can abuse
72% of MCPs allow sensitive operations such as writing to disk, executing code, or calling high-permission APIs. Most lack approval checkpoints or runtime validation. - Just two MCP plugins can push the exploit risk to 36%
Combining one MCP that processes untrusted input with another that has privileged execution rights can open the door to an exploit. With three MCPs in the system, the risk jumps to over 50%. - Installing 10 MCP plugins pushes the exploitation risk to 92%
Risk multiplies rapidly in MCP-based systems. Adding plugins without isolation or validation leaves agents highly vulnerable. - One in 10 MCP plugins is fully exploitable, and with three MCPs in a system, the chance of a silent exploit exceeds 50%
These plugins combine attacker-controlled inputs with privileged execution. - About one in eight (13%) MCP plugins accept attacker-controlled inputs from sources like web scraping, Slack, or email
These streams let adversaries inject malicious content that agents process automatically, without human review. - A real-world MCP-based agent executed attacker-supplied HTML directly into a shell with no user input
It retrieved remote HTML, fed it into a shell plugin, and ran code automatically. - Another MCP-based agent triggered silent code execution via an email-ingestion plugin paired with a code interpreter
A crafted email triggered a prompt injection that routed into code execution.
MCP Compositional Risk: The Hidden Multiplier

One plugin alone might seem harmless. But combine two or three, and suddenly you have an attack surface with no humans in the loop. From 281 real-world MCPs analyzed across open agent ecosystems:
This happens because MCPs inherit two dangerous traits:
- Untrusted inputs such as scraped web content, emails, and Slack messages.
- Privileged actions such as writing to disk, executing shell commands, or calling APIs.
When these traits intersect, even basic agents become programmable backdoors.
MCPs Present Real Exploits, Not Theoretical Flaws
This is not a theoretical problem. We observed agents that:
- Took attacker-supplied HTML, parsed it, and executed it through a shell plugin.
- Triggered code execution from a crafted email via an email-ingestion plugin paired with a code interpreter.
- Responded to a crafted Slack message that ran terminal commands via a connected automation plugin.
These were not exotic setups. They reflected common, often recommended, configurations in the agent ecosystem.
In one case, we used Claude to hack Claude, watch:
From APIs to Execution: MCPs Demand a New Security Model
MCPs are becoming the new execution layer of software, quietly replacing traditional APIs in key workflows. APIs expose data and functions. MCPs trigger actions. Many run inside local environments with deep system access and little oversight.
The security assumptions that worked for APIs do not apply here. The risk is not just in permissions, but in composition. One plugin scrapes data, another parses it, and a third executes it.
We have seen this pattern before. API sprawl led to data leakage and privilege escalation. Now, agent sprawl is creating execution risk, only this time it is faster, quieter, and harder to detect. Most MCPs lack isolation, runtime validation, or approval checkpoints. Static checks will not catch these issues. What is needed is chain-aware, context-sensitive validation that treats MCPs as active code.
What’s Next
Security teams should start reducing compositional risk by design. Recommended actions include:
- Use the MCP host approval feature to require user confirmation for every server call.
- Limit exposure by enabling only the MCP servers and tools actively in use.
- Isolate execution to contain the blast radius of high-privilege actions.
Dive Deeper into the Full Research Report
The full report ‘Quantifying Risk Exposure Across 281 MCPs’ includes the complete dataset, detailed exploit chain diagrams, platform-specific risk breakdowns, and in-depth methodology.



.svg)








.png)